Are we in India looking at the issue of ‘Hacktivism’ with the seriousness it deserves? Merely placing numerous firewalls is not adequate security. We have to discipline ourselves to eliminate in totality our culture of doing official work on our personal computers linked to the internet. Not many would have the courage to accept, but this stark truth cannot be wished away like an ostrich with its head in the sand and eyes closed. Our speed of digitisation demands absolute and total network security on one hand and on the other, we must ‘officially’ develop and sponsor an ‘army’ of Hacktivists to hack into the networks of our adversary. This ‘soft kill’ capability should then be put to use to warn the adversaries to behave or else!
The most outstanding accomplishment of human endeavour till date took place on July 20, 1969, when two mortals stepped on to the lunar surface. This monumental feat was accomplished due to advances in rocketry and colossal (at that time) improvement in computing power. Incidentally, the computing power that enabled man to reach the moon was merely equivalent to a Pentium one of present times. Computing power increases exponentially and is governed by Moore’s law, which states, “Computing power doubles every year”. X box today is nearly 1000 times faster than a Pentium One, maybe more. A physicist in the USA, who needed super computer assistance for his research but failed to buy the computer time due to prohibitive cost, found a peculiar yet workable alternative. He purchased more than 1000 X boxes, put them in parallel and achieved the computing power that was required for research.
Needless to state that computers have changed the way we live. Warfare too, has lapped up the ‘Power of the Chip’ in developing weapons and ancillary systems. With advancements in computing power, Information Warfare has assumed new dimensions. The most potent tool in the information warfare regime is not the super computers, but the ability to ‘Hack’ into a supposedly impregnable computer network protected by numerous firewalls. ‘Hacking’ has emerged as the most potent soft weapon in this era of Information Warfare. It not only destroys, corrupts, de-regulates and alters the original programme; but can also introduce undesirable inputs in the software controlling the network that may lead to catastrophe. For example, it has been alleged that Russian hackers intervened with the power grid in Ukraine in 2015, causing widespread darkness for a considerable period of time.
‘Information Warfare’ has been defined as, “Conflict and/or struggle between two or more groups in the information environment”. Computer networks depend solely on the internet. Communications also use internet or various segments of electromagnetic spectrum. The modern era of computer-based/controlled communications make every nation state vulnerable to instability by merely interfering with communication network. In order to interfere with computer networks controlling nuclear reactors, power grid, airline/railway ticketing system to name a few and virtually all other domains of almost all nations, experienced software specialists are required to attempt illegal and illegitimate transgressions into the networks.
According to a World Bank study, Russia has ‘invested’ heavily into this sphere and has over one million software specialists. Russian ‘Cyber Warriors’, another name for hackers, are amongst the most proficient in the world. It is believed that ‘officially monitored/controlled’ groups of cyber warriors numbering around three dozen are actively involved in hacking/attempt to hack other nation’s networks. It is possible or probable that this illegal gang has been provided with state immunity. Needless to emphasize that this form of warfare is more potent and can reap unbelievable benefits without being identified. When the focus shifts from systems hacking to platform hacking, it opens up far greater possibilities. Unmanned Aerial Vehicles (UAVs) and Unmanned Combat Aerial Vehicles (UCAVs) are the future platforms of aerial warfare. Imagine a scenario wherein the adversary’s UAV/UCAV is taken over by an unidentified entity and is used against the originator itself. Such eventualities are no longer fictional.
It may be of interest to mention that the P8 maritime patrol aircraft has been found to have serious ‘cyber security deficiencies’. The USAF is in the process of carrying out extensive testing of the F-22 and F-35 platforms against cyber attacks. Hackers sponsored most probably by the Iranian government recently compromised a US aerospace organisation, according to a new report from cyber security firm Fire Eye. The hackers, which Fire Eye dubs APT33, also targeted a selection of other energy and aviation bodies across Saudi Arabia and South Korea. Currently cyber attacks are confined to gathering intelligence by stealing/accessing sensitive information, defacing the home page, leaving warning messages and in few cases, espionage.
Iranian hackers have previously tried to identify computers that control infrastructure in the US, targeted a small dam in New York’s Westchester County and launched Distributed-Denial-of-Service (DDoS) attacks on US banks designed to slow service to a crawl. US authorities were able to establish that hacking operations took place during Iranian working hours and corresponded to the country’s work week of Saturday to Wednesday. Some of those other groups have used more destructive malware to wipe a target’s computers. In December last year, the Department of Defence warned US contractors about ‘Shamoon’, an Iran-linked malicious programme that wiped out thousands of computers in Saudi Arabia. The investigating team opined, “We assess there may be multiple Iran-based threat groups capable of carrying out destructive operations.”
While our relations with Iran are on the upswing, Pakistan’s association with Iranian hackers might spell trouble for us. Attribution is the most difficult thing. When we are dealing with professional hackers, it is hard to track and find real evidence of where it has come from. A group of Pakistani ‘Hacktivists’ sitting in New York, might be able to intrude into our nuclear reactors and power grids. Alternatively, a Pakistani/Chinese hacktivist might engage an ‘expert’ of unknown nationality, working for cash, to do the job.
The common belief is that the website of the National Security Agency (NSA) of the USA is one of the most impregnable networks. But the hackers of unknown nationality (possibly Russians) hacked into the website and stole ‘highly classified’ material. It stunned the US lawmakers and the intrusion in 2015, was not made public for nearly two years. The Wall Street Journal termed it as “one of the most significant security breaches in recent years”. The surprise does not end here. Detailed investigation revealed that the hack was made possible because Kaspersky Lab’s anti-virus software identified the files – a classic case of the guard being ‘hand-in-glove in the theft’. It might be termed as travesty of fate when viewed in the context that the US interfered with Iranian centrifuge network by introducing the STUXNET virus through one of the Iranian engineers who was working in the facility and was using the device on his home computer as well.
In an identical fashion, a similar act was performed when an NSA contractor took the files home without authorisation and they were accessed by attackers on that person’s home computer, which was running Kaspersky Lab’s software. The stolen material included details about how the NSA penetrates foreign computer networks, the computer code it uses for such spying and how it defends networks inside the US. The US identified Russia as the major culprit actively involved in hacking activity against the West, the US in particular. Russians are resorting to digital intrusions, which have crippled networks and they continue to refine their expertise with the knowledge gained from each such intrusion.
Are we in India looking at the issue of ‘Hacktivism’ with the seriousness it deserves? Merely placing numerous firewalls is not adequate security. We have to discipline ourselves to eliminate in totality our culture of doing official work on our personal computers linked to the internet. Not many would have the courage to accept, but this stark truth cannot be wished away like an ostrich with its head in the sand and eyes closed. Our speed of digitisation demands absolute and total network security on one hand and on the other, we must ‘officially’ develop and sponsor an ‘army’ of Hacktivists to hack into the networks of our adversary. This ‘soft kill’ capability should then be put to use to warn the adversaries to behave or else!
Although we call ourselves a ‘software super power’, the fact is that we do not produce a single computer chip. Everything is imported. Embedded virus viz Trojan Horse are known to be activated by the manufacturing country at time of their choosing. China has progressed by leaps and bounds in acquiring advanced chip technology and is in the process of developing the fastest super computer. It would be appropriate to mention the surveillance capability of the US National Security Agency while the ignoramuses, particularly politicians, are bickering over Aadhaar linking to various facilities viz PAN and mobile numbers. The US has operationalised a Global Spy System codenamed ECHELON, which has the capability to capture and monitor virtually every phone call (land line and cell phone), telex/fax anywhere in the world.
Australia, Canada, England and New Zealand are the co-partners in this US venture controlled by NSA. The ECHELON system is fairly simple in design – position intercept stations all over the world to capture all satellite, microwave, cellular and fiber-optic communications traffic, and then process this information through the massive computer capabilities of the NSA, including advanced voice recognition and Optical Character Recognition (OCR) programmes, and look for code words or phrases (known as the ECHELON “Dictionary”) that will prompt the computers to flag the message for recording and transcribing for future analysis. Intelligence analysts at each of the respective ‘listening stations’ maintain separate keyword lists for them to analyse any conversation or document flagged by the system, which is then forwarded to the respective intelligence agency headquarters that requested the intercept. But apart from directing their ears towards terrorists and rogue states, ECHELON is also being used for purposes well outside its original mission.
The regular discovery of domestic surveillance targeted at American civilians for reasons of ‘unpopular’ political affiliation or for no probable cause at all in violation of the First, Fourth and Fifth Amendments of the Constitution – are consistently impeded by very elaborate and complex legal arguments and privilege claims by the intelligence agencies and the US government. The guardians and caretakers of our liberties, our duly elected political representatives, give scarce attention to these activities, let alone the abuses that occur under their watch.
Among the activities that the ECHELON targets are:
Political Spying
Since the close of World War II, US intelligence agencies have developed a consistent record of trampling the rights and liberties of the American people. Even after the investigations into the domestic and political surveillance activities of the agencies that followed in the wake of the Watergate fiasco, the NSA continues to target the political activity of ‘unpopular’ political groups and duly elected representatives. One whistleblower charged in a 1988 Cleveland Plain Dealer interview said that, while she was stationed at the Menwith Hill facility in the 1980s, she had heard real-time intercepts of South Carolina Senator Strom Thurmond.
A former Maryland Congressman, Michael Barnes, claimed in a 1995 Baltimore Sun article that under the Reagan Administration, his phone calls were regularly intercepted, which he discovered only after reporters had been passed transcripts of his conversations by the White House. One of the most shocking revelations came to light after several GCHQ officials became concerned about the targeting of peaceful political groups and told the London Observer in 1992, that the ECHELON dictionaries targeted Amnesty International, Greenpeace and even Christian ministries.
Commercial Espionage
Since the demise of Communism in Eastern Europe, the intelligence agencies have searched for a new justification for their surveillance capability in order to protect their prominence and their bloated budgets. Their solution was to redefine the notion of national security to include economic, commercial and corporate concerns. An office was created within the Department of Commerce, the Office of Intelligence Liaison, to forward intercepted materials to major US corporations. In many cases, the beneficiaries of this commercial espionage effort are the very companies that helped the NSA develop the systems that power the ECHELON network. This incestuous relationship is so strong that sometimes this intelligence information is used to push other American manufacturers out of deals in favour of these mammoth US defence and intelligence contractors, who frequently are the source of major cash contribution to both political parties.
While signals intelligence technology was helpful in containing and eventually defeating the Soviet Empire during the Cold War, what was once designed to target a select list of Communist countries and terrorist states, is now indiscriminately directed against virtually every citizen in the world. The European Parliament is now asking whether the ECHELON communications interceptions violate the sovereignty and privacy of citizens in other countries. In some cases, such as the NSA’s Menwith Hill station in England, surveillance is conducted against citizens on their own soil and with the full knowledge and cooperation of their government. This report suggests that Congress picks up its long-neglected role as watchdog of the Constitutional rights and liberties of the American people, instead of its current role as lap dog to the US intelligence agencies.
Congressional hearings ought to be held, similar to the Church and Rockefeller Committee hearings held in the mid-1970s, to determine the extent to which the ECHELON system targets the personal, political, religious and commercial communications of American citizens. The late Senator Frank Church warned that the technology and capability embodied in the ECHELON system represented a direct threat to the liberties of the American people. Left unchecked, ECHELON could be used by either the political elite or the intelligence agencies themselves as a tool to subvert the civil protections of Constitution and to destroy representative government.
The interference of Russian hackers in the US presidential elections in 2016 is a well known fact. Hackers working for the Russian government successfully penetrated the voter rolls of a small number of states, according to Jeannette Manfra, the head of Cyber Security in the Department of Homeland Security. Manfra told NBC News that 21 states were targeted by the hackers, and an “exceptionally small number” of states were successfully accessed.
North Korea’s cyber army appears to be going after real weapons. Hackers tied to Kim Jong Un’s regime stole blueprints and other information about warships and submarines last year when they broke into one of the world’s biggest shipbuilders, according to South Korean lawmaker Kyeong Dae-soo. Blueprints, shipbuilding technology, weapons systems and test data related to submarines and destroyers were among roughly 60 classified military documents taken from Daewoo Shipbuilding last year, according to Kyeong’s office. It said it was summarising information it had received from the South Korean Defence Ministry and several military agencies. The hackers are believed to have accessed some 40,000 documents in all. Collusion between North Korea and Pakistan in this field might, rather will, spell trouble for India.
 Research & Development
Research & Development
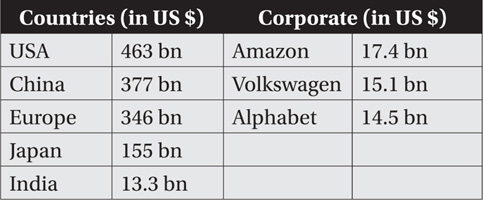
Our focus towards R&D has varied from ‘indifferent’ to ‘callous’ at best of times. A look at the R&D budget of few nations and corporate giants will tell us the complete story. Given below are the latest figures for R&D by various countries and international organisations.
In 1996, India spent 0.63 per cent of its GDP on R&D. In 2016, the figure remained the same, while China quadrupled the allocation towards R&D in the same period (0.56 per cent in 1996, 2.07 per cent in 2015).
Conclusion
Hackers are already an asset to those who want to snoop around and neutralise the adversary by ‘soft-kill’. In the foreseeable future, hackers will become a force to reckon with since nations armed with this “soft expertise” will have the capability to interfere with the operating software of ‘un-friendly’ nations at time of their choosing. A nation of expert hackers would/may challenge a much more powerful adversary having conventional and nuclear military power. Commercial espionage might just become a more potent weapon than all the weapons. India’s efforts towards becoming a nation of ‘competent hackers’ have a long way to go. We are particularly vulnerable to hacking due to our flawed propensity to “everyone keeping every record” in soft and/or hard copy. Our ‘computer discipline’ at all levels is no better than a hooligan on a street. To quote an example; during OP PARAKARAM, a software engineer purchased few hard discs from flea market in Gwalior. Lo and behold, from one of the hard discs, he was able to extract the entire war plan of the Mirage-2000. The concerned hardware had been disposed of by the logistics section of the station to a scrap dealer. From what is known in public domain, nothing substantial is being done since the powers that be believe that the word ‘hack’ is just another four letter word.





