Effective enhancement of security needs to have components that carry out continuous gapless ‘Surveillance’ of the perimeter, through day and night, in all weather and outdoor conditions (vegetation, forest, over water) and the area within. To achieve this, the system needs to ‘Detect’ the object/entity, ‘Identify’ whether it has hostile intent and if so the “What, Where and How Many” of the threat, before they can attack the targets within the airfield. All this needs to be accomplished in good time to ‘Intercept’. Once intercepted, the identity of the individual can be ascertained through other means that will be more effective.
The security system that has been envisaged will provide comprehensive, state-of-the-art and cost-effective security…
Perimeter Intrusion Detection
The Indian Armed Forces have high value assets dispersed at various locations within the perimeter of military airfields. These are high risk, high consequence of disruption facilities that need to be protected so as to prevent adverse impact on national morale besides the damage that will be caused to these assets, as revealed by recent terrorist attacks. These establishments have a large perimeter across which no entry is allowed. Intruders, who intend to breach the perimeter, should be denied entry or apprehended/neutralised in the buffer zone between the perimeter and their intended target. Prevention of intrusion through the perimeter can be divided into the following phases:
- Availability of accurate external intelligence.
- Confirmation of such intelligence from the immediate area of the airport through other intelligence sources.
- Availability of a response team of adequate strength at the desired place at the correct time.
- Engagement to apprehend/neutralise the intrusion bid.
External intelligence may not be actionable. Bolstering the intelligence that is available in the immediate area of the airport under the command and control of the security staff that is entrusted with the responsibility, can be an environment shaping tactic, as far as prevention of intrusion is concerned. In any anti-terrorist operation, intelligence is the key. Electronic surveillance systems are force multipliers in that they give an advantage to the security personnel that uses it effectively. The advantage is in terms of knowing where exactly the intrusion is likely to take place and the strength of intruders, so that an appropriate force can be dispatched/directed to engage them in good time.
Greater the accuracy of intelligence received, lesser is the deployment necessary to tackle the threat…
If the deployment of these systems is planned correctly it reduces the effort required in terms of the number of personnel deployed for protection on a regular basis or the number of mobile patrols that are needed to ascertain likely infiltration activity. These systems have the ability to provide intelligent, automated, advance warning of a likely intrusion into pre-defined areas of interest. Once these warnings are received, the required response with the requisite strength can be dispatched to engage them effectively. This will reduce the number of personnel continuously deployed or patrols in the location thereby reducing consequent costs.
Concept
This concept bolsters the traditional process of dealing with threats. It follows the continuum of surveillance, acquisition/verification, deciding whether the threat is hostile/friendly, tasking of requisite forces and apprehension/neutralisation. In the present scenario, surveillance is carried out by look-out posts; verification/reconnaissance is carried out mainly by patrols followed by engagement by the response force. Accuracy of intelligence is inversely proportional to the quantum of force that is required to apprehend/neutralise a threat. Greater the accuracy of intelligence received, lesser is the deployment necessary to tackle the threat. Along with a well-trained and adequately equipped force if surveillance and verification can be enhanced to the required level, then it becomes a lethal combination to deal with any threat. Surveillance and acquisition/verification being a tedious process and never foolproof, this system focuses on enhancing this capability, by automating this process so that there is no occasion when a likely intruder is missed and there are very few false alarms.
The most cost-effective system has all weather day/night, un-cooled thermal sensors for surveillance and visible verification cameras. The security system that has been envisaged will provide comprehensive, state-of-the-art and cost-effective security. The primary objective has been to provide a pre-emptive system that will prevent a disruption rather than conventional technologies that primarily provide forensic or post-event capabilities.
The security system needs to be a mix of men and machine…
This article suggests the use of latest generation Intelligent-CCTV (I-CCTV) technology, which is designed for pre-emption and deployment in critical outdoor locations. They provide the biggest bang-for-the-buck without compromising security. The security system needs to be a mix of men and machine. Machines/equipment that provides pre-emptive, intelligent, automated inputs need to be acted upon by men as it is always the men behind the machines that matter, in the final analysis.
The system will be integrated through an OFC network terminating at the security control centre. The signal feeds from the components will be processed, analysed, integrated, displayed and archived at the security operations centre. Alarm situations will be acted upon by the security operator/director. They may dispatch the Quick Response Team (QRT) to manage the situation depending on the need after verification. This article intends to cover surveillance, detection and verification of likely intruders into airports during day and night and in all weather conditions.
System Overview
The system will provide means for automated intelligent alerts and verification in one sensor.
Surveillance Component
Surveillance will be carried out by fixed un-cooled thermal sensors. These sensors have all-weather capability and work round the clock. They are also immune to bad weather conditions such as fog, haze and smoke. Finally, as they sense heat, they can counter visual camouflage easily. These sensors will be deployed in a ‘sentry-like mode’ i.e. will have a fixed field of view and they will be fixed in azimuth and elevation so as to cover a preselected area. Typical false alarm challenges faced by conventional systems such as moving clouds, shadows, leaves, branches and animals are eliminated intelligently and only movement of human beings, vehicles and boats in case of a water perimeter, will sound an alarm. The deployment should be so planned that there is minimum blind areas in the Line of Sight (LoS) of these sensors.
Verification Component
When the alarm is generated by the surveillance sensors, a High Definition visible camera will capture the details such as strength. This is supported by IR illuminators for night capability.
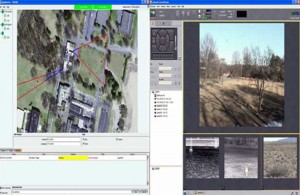
Figure 1: Security Operators Console. The suggested console will have two views as shown above. The Right View will show live video imagery from multiple cameras, where the cameras with live action can automatically be prioritized. The Left View is a Bird’s Eye View of the facility showing camera coverage areas and any moving intruder is shown as a moving red dot, at its true GPS location.
The coordinates (Latitude/Longitude or grid reference) of the intrusion can also be made available with the exact location of individual intruders on an aerial view. Based on this input the response force can be designed and directed to deal with the threat. The integrated system will automatically alert the observer when a threat in the form of a human being, vehicle or boat enters the footprint of the sensor eliminating all false alarms and verify the strength of the threat so that appropriate action can be planned and executed. The observer will be able to see the Field of View (FoV) of the Surveillance sensor, FoV of Verification cameras and the location of intruders on an aerial view on his monitor as shown in Figure 1.
Perimeter Intrusion – Airfields
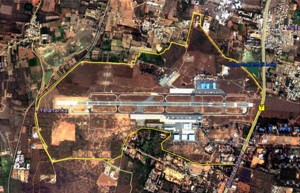
The perimeter that has been assumed for planning purpose is indicated in Figure 2. Any deviation will need re-planning.
The suggested deployment is in Figure 3.
The red icons indicate the location of fixed un-cooled thermal cameras. The area covered by the yellow triangles is the footprint of the thermal sensors and a gap less overlapping coverage is ensured.

Figure: 3 Gapless Perimeter Surveillance for an airfield. Each yellow triangle above represents a fixed thermal camera and the circular icon shows the range of verification component in the direction of the thermal component
The red triangles, close to the icons are blind zones at the feet of the camera. These are covered effectively by the footprint of the camera that is behind. The grey icons with brown rings around them represent the range of verification component. Since the effective range of these sensors is quite large the number of sensors required is few and the total project costs reduce due to savings in infrastructure such as poles and power. A close up view of one segment of the perimeter is as shown at Figure 4,
As the cameras are deployed along the perimeter wall, their FoV (width) is arranged to cover areas both outside and inside the perimeter wall. In this design, the minimum distance at which an intruder can be detected outside the boundary wall will be 20m. This warning is adequate for a response team to be dispatched for effective action as the boundary wall acts as a delay line. By the time the intruders scale the boundary wall the team will be in a position to cordon off that area. In case greater warning stand-off is desired camera positions can be altered to do so and more cameras maybe required. The area within the yellow triangle indicates the area within which the intruder can be tracked even if he intrudes into the airport. Intruders cannot approach the base of any camera without the camera behind generating an alarm and being intercepted. In this manner cross cover is provided by cameras to ensure a gap less perimeter coverage.
Functional Characteristics
It is critical to define the key functional requirements before designing the solution. This is perhaps the most important part, as designing functional requirements requires a simultaneous and in-depth understanding of security requirements as well as of the state-of-the-art in electronic security technology. These requirements should be the “Heart and Soul” of any system developed. With the installation of this IP based system, the following objectives are intended to be achieved.
It is critical to define the key functional requirements before designing the solution…
• Early, Wide Warning Zone. The system shall provide detection and alerting against human and vehicle-sized intruders, in a 3D zone within at least 20m on both sides of the fence-line and above.
• Reliable Alerts. The system is to detect all intrusions with very low false alerts, in environmental conditions ranging from clear day light to all weather and all lighting conditions including low light up to dark moonless night (0 lux), dawn/dusk and cloudy skies, fog and rain.
• Automated Verification. The system is to provide for hands-free intruder verification and tracking of target throughout its footprint. System shall cater for automated re-acquisition and continuous tracking independent of temporary occlusions.
• Continuous Automatic Intruder Tracking. The intruder needs to be automatically tracked continuously for at least 20m before and 20m after fence line/ boundary wall in three dimensions for seamless handover to quick response team.
• Situational Awareness. The system is to provide an aerial view of intruder’s location. Geo-registered rectangular coordinates shall be continuously reported right from the detection sensor, along with intruder tracking information. Such information could be sent directly to quick reaction team and control centre for quick response without human intervention.
Empirical studies have proved that the attention span of a person watching a monitor is not greater than 22 minutes…
• Multi-sensor Co-ordination and Handover to QRT. The system is to have the capability to carry out target tracking using its geo-registered rectangular co-ordinates to enable correlation between multiple sensors, camera, microwave and radar including easy sensor-to-sensor handover and multi-sensor validation.
• Full-IP architecture. The system is to be of full IP for easier integration with other systems and operations. The system is to use Standards-based IP architecture (non proprietary).
• Interoperability. The system is to provide seamless integration of PIDS with Security Operations Centre (SOC) without middleware or custom integration.
• Scalability. The system should be capable of linear scalability without additional central processing hardware. There shall exist the possibility of expanding the configuration of the system by integrating a new Camera or Monitor into the system. The system should be scalable to enterprise level so that it is operative at different locations seamlessly.
• Environmental Protection. Each sensor enclosure is to be sealed, nitrogen filled and pressurised, to prevent moisture incursion.
• Maintainability. All equipment shall be designed to ensure continuous satisfactory operation of not less than fifteen years under the environmental conditions specified.
• Zones. The system’s field of view can be divided into a collection of independent zones or regions, each with the ability to specify different alert criteria. Zones shall be capable of being designated as alarm or mask types.
The surveillance system needs to be ‘Intelligent’ in that it should be able to weed out false alarms that are generated due to moving clouds…
• Analytic Modes. The system shall provide the following Analytic Modes that are programmable with ease in the field of view of the sensor:
. • Time-based alert policies
. • Motion zone
. • Multi-Mode tripwire
. • Directional Zone violation
. • Loitering
. • To and From zone
• Target Attributes. The system shall provide the following Target Attributes and analytic modes that are programmable with ease in the field of view of the sensor:
. • Height
. • Width
. • Speed
. • Direction
. • Aspect-ratio
. • Absolute Geo-registered Rectangular Coordinates (Lat/Long, Grid Reference)
Surveillance of Areas Within
After the intrusion, if the intruder manages to evade interception and comes into zone where surveillance is not available, another system provides area coverage. This system can be integrated at the SOC with ease. It consists of a rotating thermal camera mounted on a mast to provide uninterrupted coverage of the area of interest in all weather and day/night conditions. This system can also detect drones, low flying small aircraft etc which tend to breach the perimeter by air.
The cost of such systems would be in the region of 0.2 to 0.3 per cent of the value of the assets being protected. A small price to pay for enhancing security.
Cost Factor
The cost of such systems would be in the region of 0.2 to 0.3 per cent of the value of the assets being protected. A small price to pay for enhancing security.
Conclusion
Effective enhancement of security needs to have components that carry out continuous gapless ‘Surveillance’ of the perimeter, through day and night, in all weather and outdoor conditions (vegetation, forest, over water) and the area within. To achieve this, the system needs to ‘Detect’ the object/entity, ‘Identify’ whether it has hostile intent and if so the “What, Where and How Many” of the threat, before they can attack the targets within the airfield. All this needs to be accomplished in good time to ‘Intercept’. Once intercepted, the identity of the individual can be ascertained through other means that will be more effective.
Empirical studies have proved that the attention span of a person watching a monitor is not greater than 22 minutes. Registering any matter of consequence if he is given an array of 16 camera views is impossible. The surveillance system needs to be ‘Intelligent’ in that it should be able to weed out false alarms that are generated due to moving clouds, their shadows and animals; ‘automatic’ so that it provides an alert automatically when a target of interest is detected so that the Officer On Duty (OOD) is free to attend to other tasks on hand and look at the screen (Figure 1) only when an alert is sounded. This solution suggests installation of a system with intelligent, automatic, un-cooled thermal sensors as it will suit static establishments the best. It will be all weather with true Day and Night capability.







Well written Johnson.
Permit to add somethings.
There are state of the art cameras available in the world which have a capability to cover a wider area.Obviously the intruder would like to operate from the least expected ingress routes.Moreover,the entire perimeter cannot be having sentries at arm length at all besides the patrolling teams.So,such cameras should be able to detect and thereby help prevent intrusion of any kind.The intruder could even make use of the drones;which again could be detected by the latest equipment.
For the airfields,suggest that QRTs specially selected from the Army be stationed permanently,which could take action within a short span of time.And this short span of time will have to be dictated by an efficient,timely and accurate intelligence.
Similarly for the civilian airports, but with CISF personnel.