In the late 1930s, a famous radio program in the USA called War of the Worlds — a story line that proposed an attack on the earth from Mars — created a sensation and instilled fear into the listening audience. Those were simpler times and ours is — hopefully — a more sophisticated and global situation. However, the proposition of attacks on the homeland is no less cogent today. My purpose in this presentation is not to scare anyone, but to provoke strategic dialogue using a totally theoretical scenario — generated in keeping with the overall theme of this conference — by computer.
 My colleagues and I have set the venue close to home — perhaps uncomfortably so — to make a point: it could happen here! For the purposes of this presentation, the setting is an attack from the sea against the west coast of India targeting the high value and critically important oil drilling facilities of the Bombay High and the nuclear facilities at Trombay. The scenario underscores the requirement for “intelligence, reconnaissance and surveillance” — ISR if you will — as important contributions to national security. It also highlights the role that netcentric operations play in maximizing efficiency while minimizing — I use this last term advisedly — cost. The whole purpose of netcentricity, as we all know, is to make the best use of available assets.
My colleagues and I have set the venue close to home — perhaps uncomfortably so — to make a point: it could happen here! For the purposes of this presentation, the setting is an attack from the sea against the west coast of India targeting the high value and critically important oil drilling facilities of the Bombay High and the nuclear facilities at Trombay. The scenario underscores the requirement for “intelligence, reconnaissance and surveillance” — ISR if you will — as important contributions to national security. It also highlights the role that netcentric operations play in maximizing efficiency while minimizing — I use this last term advisedly — cost. The whole purpose of netcentricity, as we all know, is to make the best use of available assets.
While several of the tactical ISR elements I have chosen to portray as nodes on the netcentric mechanism are — or are modeled after — Northrop Grumman surveillance systems, this is not meant to be a sales pitch and you will find very little technical data in the presentation. The emphasis will be on what is required to maintain vigilance and security of vital sea-land interfaces and crucial installations. Northrop Grumman just happens to be in the forefront of this challenge.
We have learned from the events of Nine Eleven and more recently — and closer to home — how hard it is to predict random acts of terrorism. In just the last few weeks, latter day pirates in the waters off Somalia boarded and seized a merchantman and held the crew and contents for ransom. While not “terrorism” per se, the incident provoked responses from countries around the Indian Ocean littoral and the Government of India has dispatched a frigate to participate in the international effort to control piracy.
The meat of the presentation is taken from a modeling and simulation exercise developed by our Cyber Warfare Integration Network to test the reaction and planning skills of the players in the exercise. Before I run the scenario, a word about what you will see. It may all look like entertainment or a training film for operators, but what it is in the hands of the “modelers” is a planning tool that can be manipulated behind the scenes to see whether plans make sense or need modification. The viewers in a war game can be challenged or second-guessed to make whatever point the planners want to emphasize.
The simulation you will be seeing is the animated portion of the overall simulation. Analytical data is being generated by these models that can be stored, replayed, or even repeated using slightly different weapon parameters. In addition to analytical studies, tools such as the CWIN can be used for training of senior officers in the decision-making process. While every real-world scenario is unique and calls for sound judgment based on the individual situation, the use of computer simulation, such as CWIN, can be used to explore alternatives and the grounds for operational-level professional discussion.
 In the scenario we have chosen to portray today, we have posited that an “innocent” merchantman is on the high seas bent on creating an incident — and inflicting damage — on a vital Indian installation. Let’s just say that the targeted installation is an oil platform in the Bombay High or, more ominously, the Homi Bhabha Research Center at Trombay. Our Navy [and Coast Guard] has no way of knowing which among the many ships innocently plying the crucial Arabian Sea/Indian Ocean waterway is the “bad guy”. Our scenario today portrays what is needed among the available technologies to — hopefully — sort out the wheat from the chaff and prevent the attack that our intelligence services believe to be imminent.
In the scenario we have chosen to portray today, we have posited that an “innocent” merchantman is on the high seas bent on creating an incident — and inflicting damage — on a vital Indian installation. Let’s just say that the targeted installation is an oil platform in the Bombay High or, more ominously, the Homi Bhabha Research Center at Trombay. Our Navy [and Coast Guard] has no way of knowing which among the many ships innocently plying the crucial Arabian Sea/Indian Ocean waterway is the “bad guy”. Our scenario today portrays what is needed among the available technologies to — hopefully — sort out the wheat from the chaff and prevent the attack that our intelligence services believe to be imminent.
The story opens with an overview of the sea-land interface emphasizing the multitude of potential targets. We see the depiction of a couple of radar sweeps symbolizing what probably are numerous surveillance assets — friendly and otherwise — that inhabit the nearby seas on a routine basis. But how do we pick out the bad guy from the welter?
This is where the nodes on the netcentric capability come into play. It is difficult to display visually the abstract web of communications that constitute “netcentricity”. Let’s just stipulate that they are there and concentrate on the hardware that provides the eyes and ears of a meaningful intelligence, reconnaissance and surveillance — ISR — system.
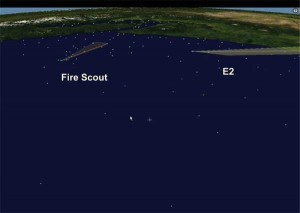
A modern and meaningful ISR system comprises of manned and unmanned platforms and I will introduce them to you in no particular order. The first is a vertical takeoff unmanned aerial vehicle — VTUAV — symbolized by the Fire Scout. The US Navy is in the advanced stages of acceptance testing of the Fire Scout B-model that will become operational in the maritime services next year.
The VTUAV is the new “close examination” asset in the maritime surveillance kit. It can operate – takeoff and land – from the smallest seaborne helicopter platform day or night, even in heavy weather. My remarks, of course, focus on the attributes and capabilities of the Fire Scout, but many of these same attributes would be common to any VTUAV using currently available designs and technologies. The main features of these systems are persistence and reach, low noise and visible signature and above all, simplicity. Competent VTUAV design forgoes many of the crew-protection redundancies extant in manned helicopters — no need since there are no humans aboard. The human fatigue factor is also avoided. The newest VTUAV designs can carry a multiplicity of payloads — SAR radar, electro-optical and IR sensors, laser designators, etc. They do the job of close examination of potential targets — down to reading the names and registrations of maritime targets for positive IDs. What is perhaps even more attractive is the relative ease of maintenance of current-generation VTUAVs. Fire Scout, for example, requires only one hour of maintenance per flight hour, unheard of in the helicopter community from which I come.
 Apart from the present scenario, VTUAVs provide an ideal solution for the “other” maritime security adjuncts: the Coast Guards, customs services and other waterborne police organizations. Here again, small size, reduced personnel and maintenance requirements, etc, make the VTUAV the ideal platform for drug interdiction, search-and-rescue and anti-pollution patrols.
Apart from the present scenario, VTUAVs provide an ideal solution for the “other” maritime security adjuncts: the Coast Guards, customs services and other waterborne police organizations. Here again, small size, reduced personnel and maintenance requirements, etc, make the VTUAV the ideal platform for drug interdiction, search-and-rescue and anti-pollution patrols.
Next we go to the opposite end of the end of the sophistication and lethality spectrum: the tactical aircraft that will be the instrument for execution of the tactical response plan – that will take out the “bad guy” once he is singled out from the many other targets in the area of operations. We have chosen to show the US Navy’s F/A-18 in this role since it is a multi-purpose tactical aircraft well-known to the Indian Navy from joint maneuvers [like the just-completed Malabar exercise for this year] and is under consideration by the Indian Air Force as the future Medium Multirole Combat Aircraft. It could have as easily been the Indian Navy’s current Harrier jumpjet or the IAF’s Su-30.




