New threats and technologies are giving rise to terms such as spectrum warfare that seek to blend electronic warfare, cyber warfare and other technological approaches to controlling the RF spectrum.
Environment Scan
Chinese and Russian exploitation of cyberspace, however, is not solely limited to information warfare…
In 1991, the rapidity and perceived ease with which the United States demolished the Iraqi army shocked Russia and China. To counter the United States, other states began investing in information warfare capabilities — Electronic Warfare and Computer Network Operations — to try to retard the US ability to use cyberspace for military operations. These strategies mesh with existing usage of anti-access and area denial weapons and counter space capabilities, the employment of special operations and airborne units, and other similar low-cost/high-value tools. Unlike many in the US, Russia and China do not see cyber warfare tactics and operations as stand-alone strategic methods.
China’s information warfare theory and doctrine is well-known. Chinese strategists contemplate attacks on military and civilian infrastructure in concert with deception operations and conventional weapons. The Russians have developed a similar set of ideas and doctrine rooted around concepts of reflexive control, which employs integrated deception and cyber operations. Both states maintain military and intelligence structures for employing information warfare but also have a murky relationship with patriotic hackers and cyber criminals who engage in espionage and political subversion.
Chinese and Russian exploitation of cyberspace, however, is not solely limited to information warfare. Rather, both states have also attempted to “informatise” their own armed services. Informatisation in Chinese and Russian military doctrine should be understood as a structural integration of modern information technology with existing and future military platforms. Chinese military writings in particular portray “informatisation” as the digital equivalent of motorising land armies in the inter-war period.
Electronic Warfare and Computer Network Operations both target, in different ways, a military force’s ability to employ cyber power on the battlefield…
Other states and non-state actors pursue information warfare capabilities and means of exploiting cyberspace for powerful conventional weapons. North Korea and Iran are building up hacking and electronic warfare capabilities to counter the West and target their neighbours. North Korea has executed cyber-attacks against South Korean civilian targets, jammed air traffic communications and more recently attacked Sony Entertainment Company. Iran is believed to have carried out cyber attacks on the USA financial services and the Saudi oil facility using Shamoon virus and claims to have used Electronic Warfare to down an American spy drone. Non-state actors are engaging in what former Israeli Defense Forces commander Itai Brun called, “The Other Revolution in Military Affairs” using cyberspace as a medium for distributed operational command-and-control, communications, sensor networks and propaganda. The proliferation of precision-strike weapons predicted by many military analysts may add a kind of primitive non-state reconnaissance-strike complex to this mixture of cyber-enabled tactics and operations.
The Operational Environment (OE)
The Operational Environment (OE) has changed dramatically. Unprecedented levels of adverse activity in and through cyberspace threaten the integrity of nation’s critical infrastructure, financial systems, and elements of national power. These threats range from unwitting hackers to nation-states, each at various levels of competence. Collectively, the threats create a condition of perpetual turbulence without traditional end states or resolution.
The ever-increasing rate of technological advances and its wide proliferation make it increasingly difficult to achieve success across the military Full Spectrum Operations (FSO). The convergence of wired, wireless and optical technologies has led to the merging of computer and telecommunication networks; handheld computing devices continue to grow in number and capability. Next generation systems are beginning to emerge, forming a global, hybrid, and adaptive network that combines wired, wireless, optical, satellite communications, Supervisory Control And Data Acquisition (SCADA) and other systems. Soon networks will provide ubiquitous access to users and enable them to collaborate when needed in near real time. Consequently, the current vocabulary, including terms such as Computer Network Operations (CNO), Electronic Warfare (EW) and Information Operations (IO) will become increasingly inadequate.
Computer Network Operations (CNO) is one of the sword arms of the Information Warfare (IW)…
Full Spectrum Operations (FSO) will encompass three interrelated dimensions each with its own set of causal logic and requiring focused development of solutions:
- First dimension – The first dimension is the psychological contest of wills against implacable foes, warring factions, criminal groups and potential adversaries.
- Second dimension – The second dimension is strategic engagement and involves keeping friends at home, gaining allies abroad, and generating support or empathy for the mission in the area of operations.
- Third dimension – The third dimension is the cyber-electromagnetic contest. Trends in wired, wireless and optical technologies are setting conditions for the convergence of computer and telecommunication networks. This dimension focuses on gaining and maintaining an advantage in the converging mediums of cyberspace and the Electro-Magnetic Spectrum (EMS).
Computer Network Operations
Computer Network Operations (CNO) is one of the sword arms of the Information Warfare (IW) which is defined as, “actions taken to achieve ‘information superiority by adversely affecting the adversary’s information, information-based processes, information systems, and computer-based networks whilst simultaneously protecting one’s own information, information-based processes, information systems and computer-based networks.” The seven forms of IW mentioned in the Indian Army doctrine are Command and Control Warfare (C2W), Intelligence Based Warfare (IBW), Electronic Warfare (EW), Psychological Warfare, Cyber Warfare, Economic Information Warfare and Network Centric Warfare (NCW). Cyber warfare is conducted through CNO in the cyber space using cyber power.
Cyberspace is an operational space where humans and their organisations use the necessary technologies to create effects…
Cyberspace is defined (by the USA) as, “a domain characterised by the use of electronics (ICT and Media) and the Electro Magnetic Spectrum to store, modify and exchange data via networked systems and associated physical infrastructure.” Civilians, terrorists and the military operate in this cyberspace to conduct their business and/or operations.
Cyberspace is an operational space where humans and their organisations use the necessary technologies to create effects, whether solely in cyberspace or in and across the other operational domains and elements of power. It is an operational medium through which “strategic influence” is conducted. The fundamental condition of cyberspace is the blending of electronics and electro-magnetic energy.
Worldwide, people and in some cases, the governments are engaged in the exploitation of cyberspace for illegal activities such as espionage, theft of technology, financial frauds and so on. They have, accordingly, developed means and methods to carry out such activities by way of viruses, root kits, malware and so on. This evolving threat to society manifests in the ability to disrupt networks, systems and their functionality and their suitability for the conduct of asymmetric warfare by attacking Critical Information Infrastructure.
Cyber power is the use, the threatened use or effect by the knowledge of its potential use, of disruptive cyber attack capabilities by a nation state. Nations may project cyber power in a number of ways – in concert with kinetic operations, masked and with no clear link to the attacker, as part of complex military-diplomatic escalation, or in indirect manners to exert influence or advance national goals. CNOs are the instrument of application of cyber power in cyberspace. These, in concert with EW, the other sword arm of IW, are used primarily to disrupt, disable, degrade or deceive an enemy’s command and control and critical information infrastructure thereby crippling the enemy’s ability to react and make effective and timely decisions, while simultaneously protecting and preserving own Command and Control and critical information assets.




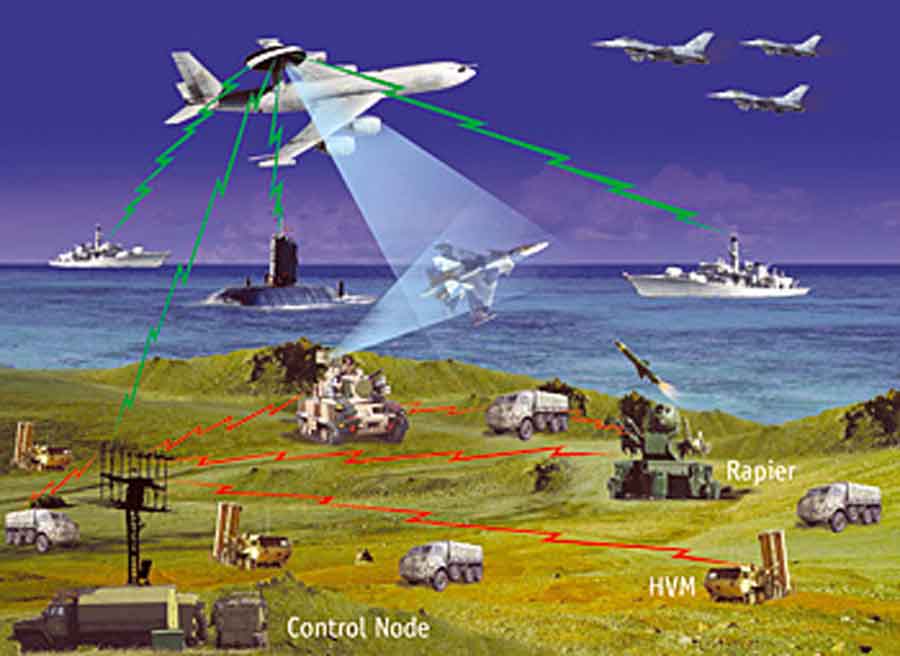


” Cyberspace is defined (by the USA) as, “a domain characterised by the use of electronics (ICT and Media) and the Electro Magnetic Spectrum to store, modify and exchange data via networked systems and associated physical infrastructure.” Civilians, terrorists and the military operate in this cyberspace to conduct their business and/or operations. ” –
It seems there is big confusion here with “technological” terminology. The naming “cyber” derives from the usage of the concept of “cybernetics” first invented by the mathematician Norbert Wiener Professor in MIT in 1940s.Those were days of dawning of technological revolution. It is difficult to go into the depth of scientific knowledge to bring out how “cyberspace” is related to “cybernetics”, but suffice it say that in normal parlance “cyberspace” implies a system of connected communication systems , e.g. computers in the internet linked by broadband technology. Of course “communication” is the at the core in military operation in the battlefield which is often classified under “netcentric” warfare, a very secret area in the western armed forces. But technically, electromagnetic spectrum control does not fall into this nor does Electronic Warfare whose main aim is for surveillance and countermeasures directed against the enemy..
Read more at:
https://www.indiandefencereview.com/news/computer-network-operations-and-electronic-warfare-complementary-or-competitive/0/
Thank You sir for sharing so much helpfull article. Thanks a lot